In crypto, losses do not come with warnings. There is no fraud department, no reversal button, no customer support that can restore what is gone. When I lost $136,000 in a single exploit, it was not because I was careless. It was because I underestimated how sophisticated the threat landscape had become.
That loss forced me to redesign everything. What emerged was not just better storage, but a layered security architecture built around one principle: assume compromise is always possible.
Here is the system.
1. Understand the New Threat Model
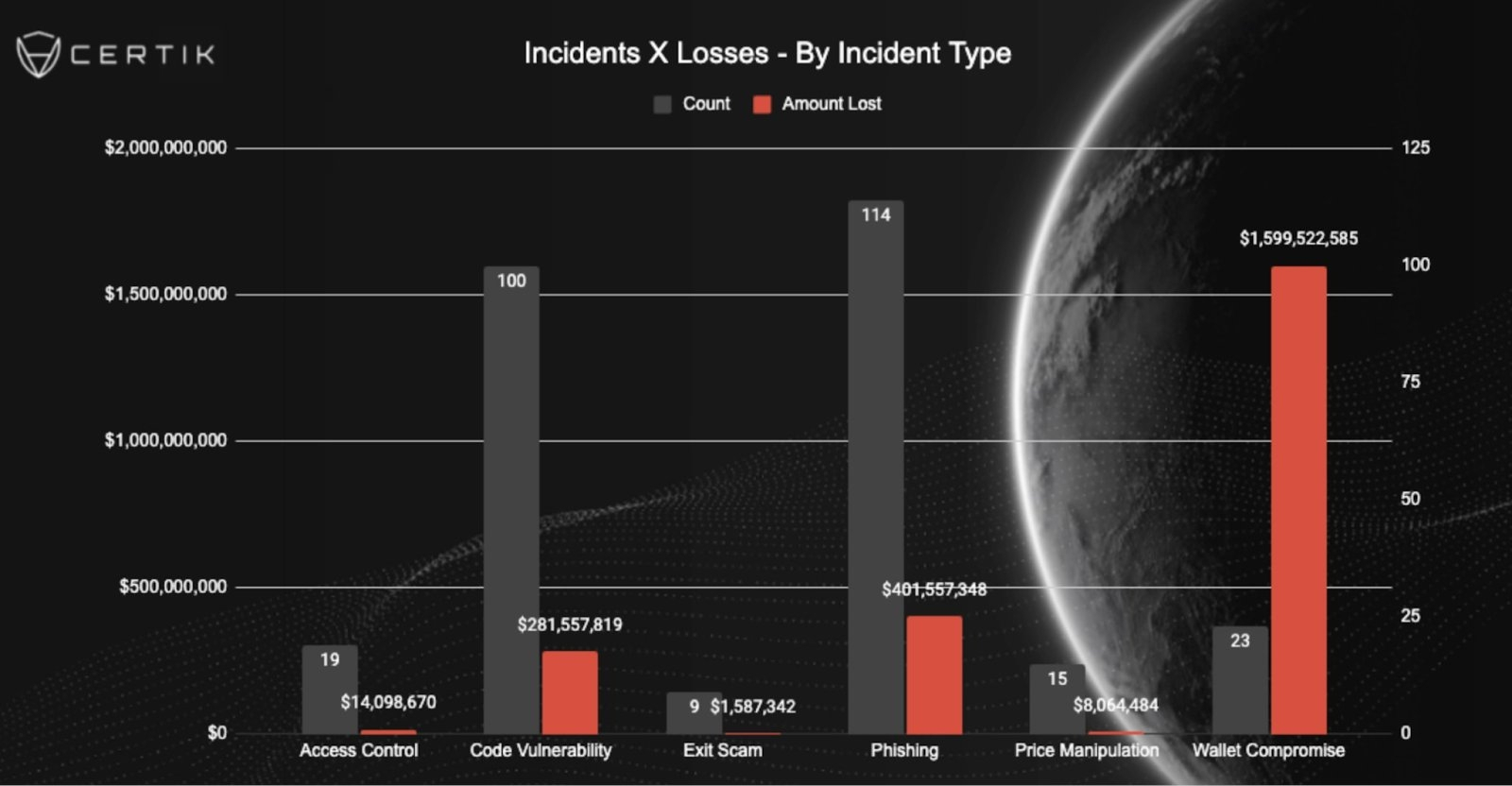
Crypto attacks in 2025 are no longer simple phishing emails. AI-generated scams, malicious smart contracts, wallet drainers embedded in fake social posts, and cloned decentralized applications are everywhere. If you interact on-chain, you are a potential target. Security begins with paranoia, not convenience.
2. Treat Your Seed Phrase as Absolute Authority
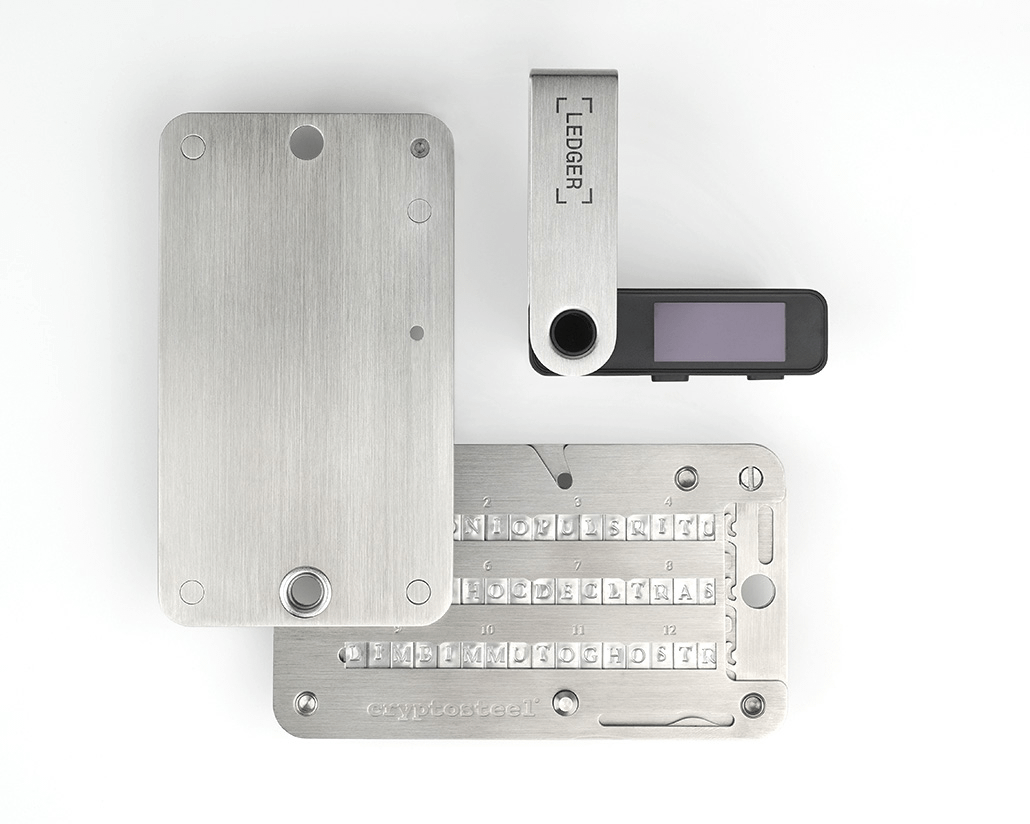
Your seed phrase is your wallet. Whoever controls it controls everything. It should never be photographed, typed into cloud storage, saved in password managers, or stored digitally in any form. The only acceptable formats are physical, preferably metal backups resistant to fire and water. Multiple copies stored in separate secure locations reduce single-point failure risk.
3. Separate Storage by Function
The biggest mistake I made was using one wallet for everything. Now the structure is strict. A cold wallet stores long-term holdings and never connects to risky applications. A hot wallet handles routine transactions. A burner wallet interacts with experimental dApps, mints, and unknown contracts. Exposure is compartmentalized. If the burner is compromised, the core remains untouched. This rule alone prevented another five-figure loss later.
4. Hardware Is Mandatory, Not Optional
Browser wallets alone are insufficient for meaningful capital. Hardware wallets such as Ledger, Trezor, Keystone, or air-gapped devices dramatically reduce remote attack surfaces. Cold storage is not about convenience. It is about eliminating entire categories of risk.
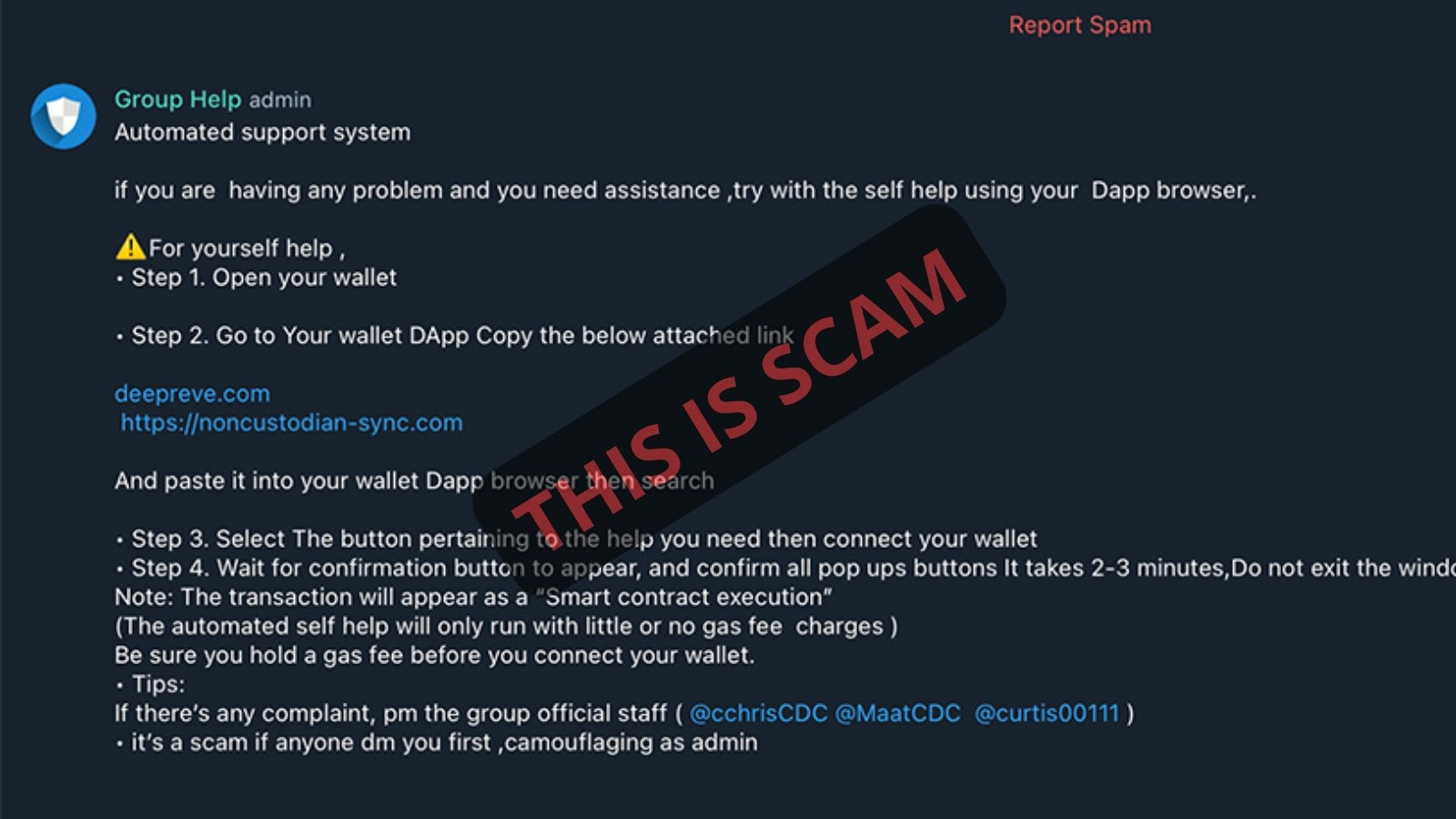
5. Assume Every Link Is Malicious
Fake websites can perfectly replicate legitimate platforms. Search engine ads and social media links are frequently weaponized. Access important platforms through bookmarked URLs only. Verify domains carefully before signing any transaction.
6. Control Smart Contract Permissions
Every token approval grants spending rights. Many users forget that these permissions persist indefinitely. Regularly auditing and revoking unused approvals reduces exposure dramatically. Security is not a one-time setup. It is maintenance.
7. Strengthen Account-Level Protection
Text message two-factor authentication is vulnerable to SIM swap attacks. Authentication apps or hardware security keys provide stronger protection. Every exchange account, email, and connected service must meet the same standard.
8. Remove Counterparty Dependency
Funds left on exchanges are not under your control. Platform freezes, insolvency, or breaches can block access instantly. Self-custody is not ideology. It is risk management.

9. Build Redundancy and Recovery Plans
Backups must survive theft, fire, and natural disasters. The three-two-one principle applies well: multiple backups, stored in different physical locations, with at least one offsite. Additionally, plan inheritance structures so assets are accessible to trusted parties if something happens to you.
10. Conduct Routine Security Audits
Once a month, review wallet history, revoke unnecessary permissions, verify backup integrity, and reassess exposure. Complacency is the silent vulnerability that eventually costs the most.
The hardest lesson I learned is that in crypto, one mistake is enough. Years of caution can be erased by a single signature on a malicious contract.
There is no safety net. No recovery desk. No forgiveness from the blockchain.
Security is not a product you buy. It is a system you design and a mindset you maintain.
In crypto, you are not just the investor. You are the bank, the vault, and the security team.

