Category: Market Structure · Infrastructure Research · On-chain Data
Data updated: February 2026
Executive Summary
Crypto’s foundational commitment to transparency solved an early trust problem. At scale, however, transparency has evolved into an exploitable surface.
With Ethereum processing between 1.2–2.6 million transactions per day in 2025–2026 and cumulative extracted MEV exceeding $9 billion, open execution environments increasingly resemble adversarial microstructure arenas rather than neutral settlement layers.
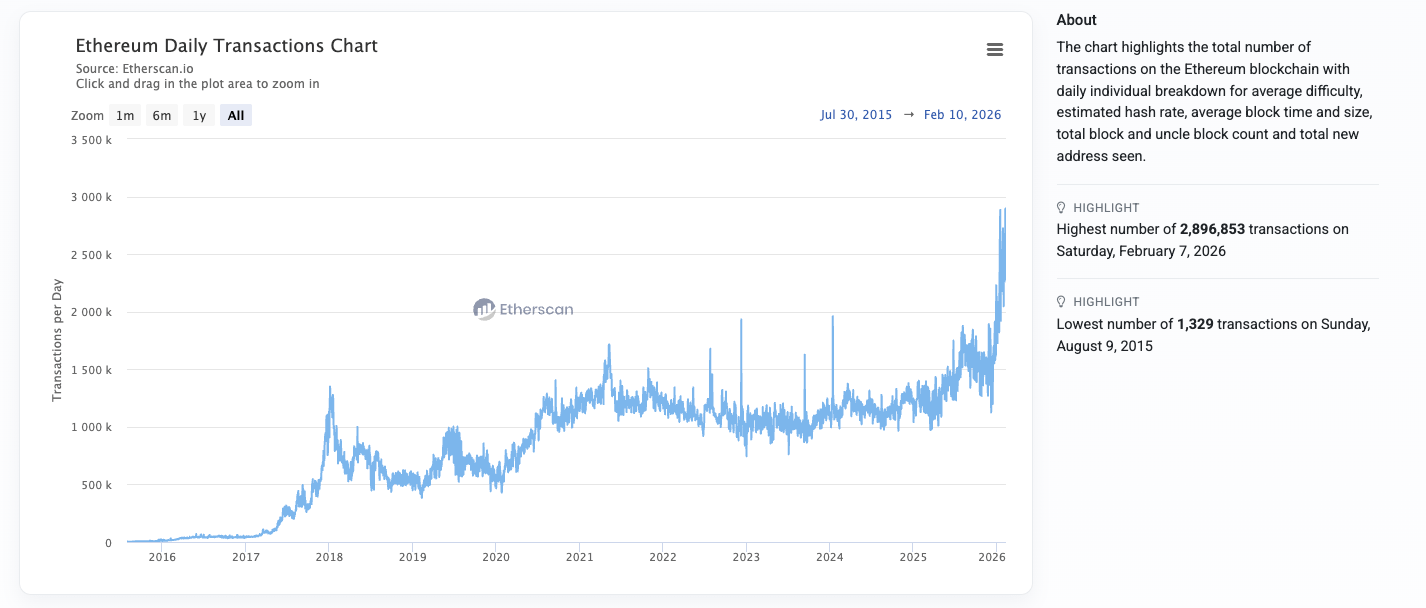
Privacy is no longer an ideological debate about anonymity. It is an infrastructure requirement for capital preservation, execution integrity, and institutional participation.
The next phase of market evolution is not “private vs public,” but verifiable confidentiality, enabled by the integration of Zero-Knowledge (ZK) systems and Fully Homomorphic Encryption (FHE).
1. Macro Context: Capital Density Changes Everything
Between 2020 and 2025, digital asset markets transitioned from retail-dominant experimentation to capital-dense, infrastructure-heavy ecosystems.
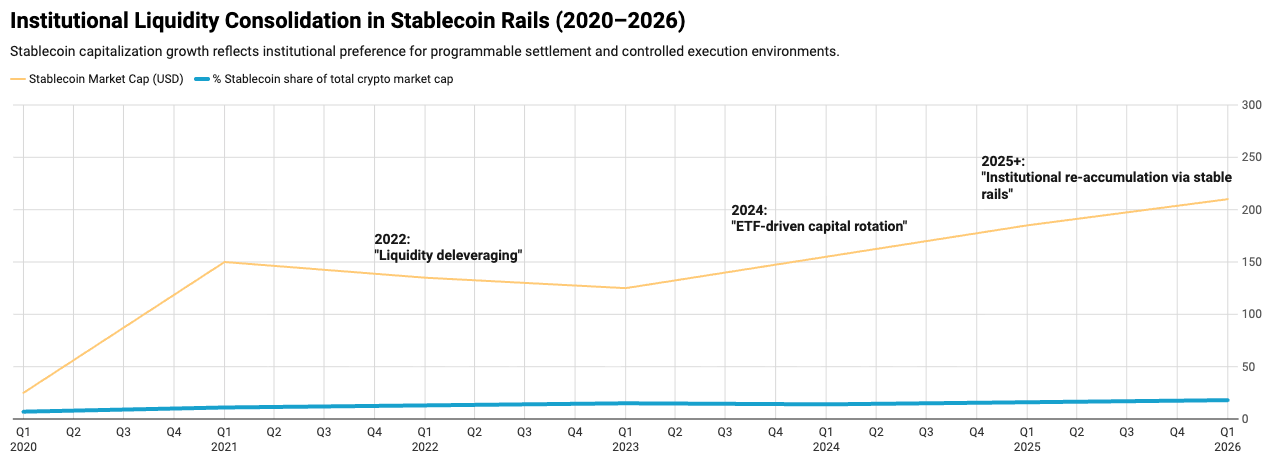
Stablecoin supply surpassed $150B+ across chains.
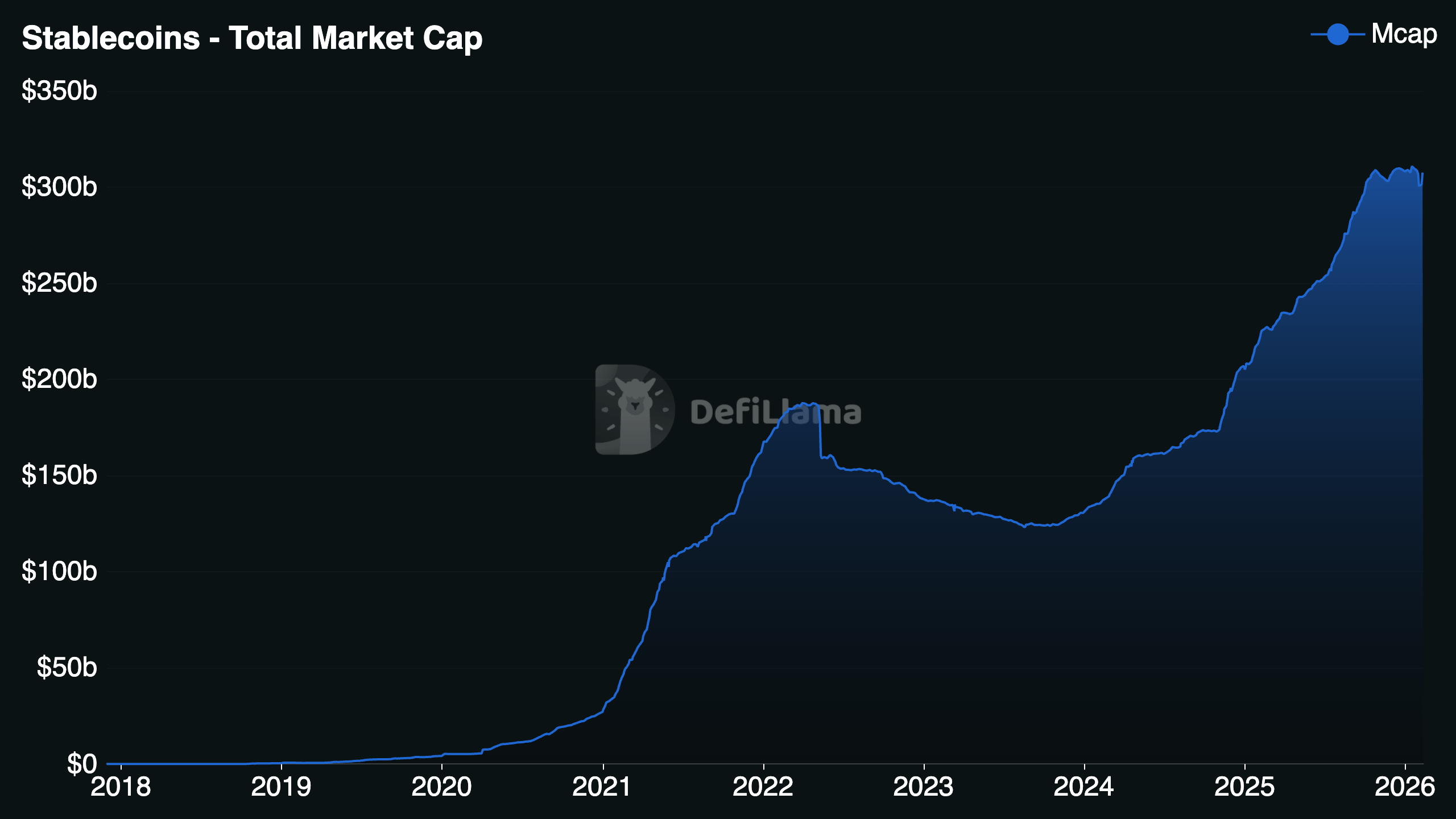
Stablecoin market cap expands structurally since 2020. DeFi TVL periodically exceeded $80–120B depending on market cycle.
Institutional desks, ETFs, and structured products expanded exposure to crypto-linked assets.
At low capital density, transparency fosters trust.
At high capital density, transparency invites extraction.
Market structure shifts once blockspace becomes economically valuable.
2. MEV: Transparency as Economic Leakage
Maximal Extractable Value (MEV) represents the clearest quantification of transparency-induced leakage.
As of early 2026:
Cumulative MEV extraction on Ethereum exceeds $10B.
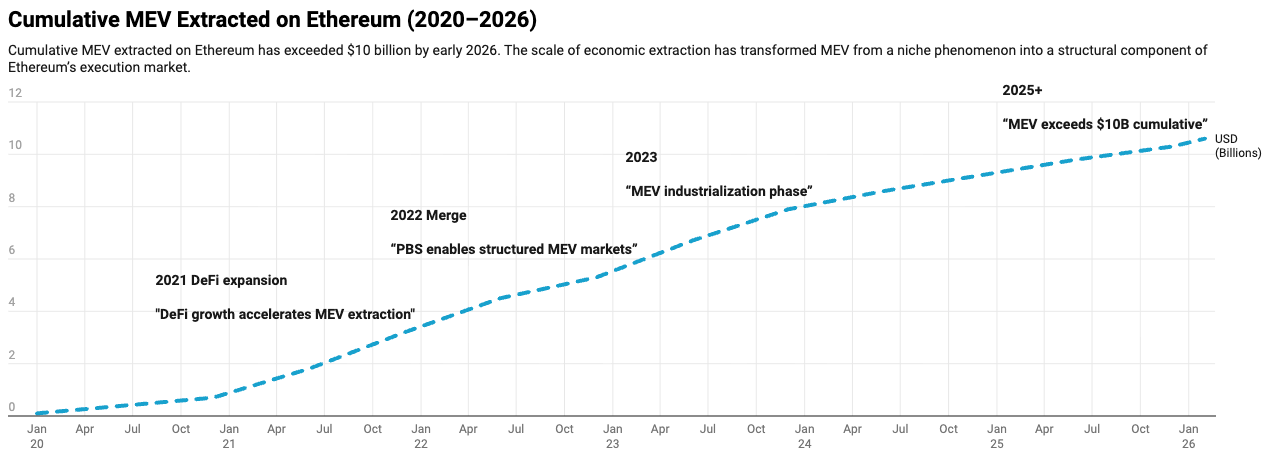
Cumulative MEV extraction on Ethereum exceeds $10B (2026). During volatile periods, daily extraction fluctuates between $15M–$25M.
Sandwich attacks account for roughly 30–35% of toxic flow, with hidden slippage typically ranging from 0.5% to 1.5% per affected swap.
In peak liquidity windows, bot-controlled addresses often outnumber organic users 2–3x in major AMM pools.
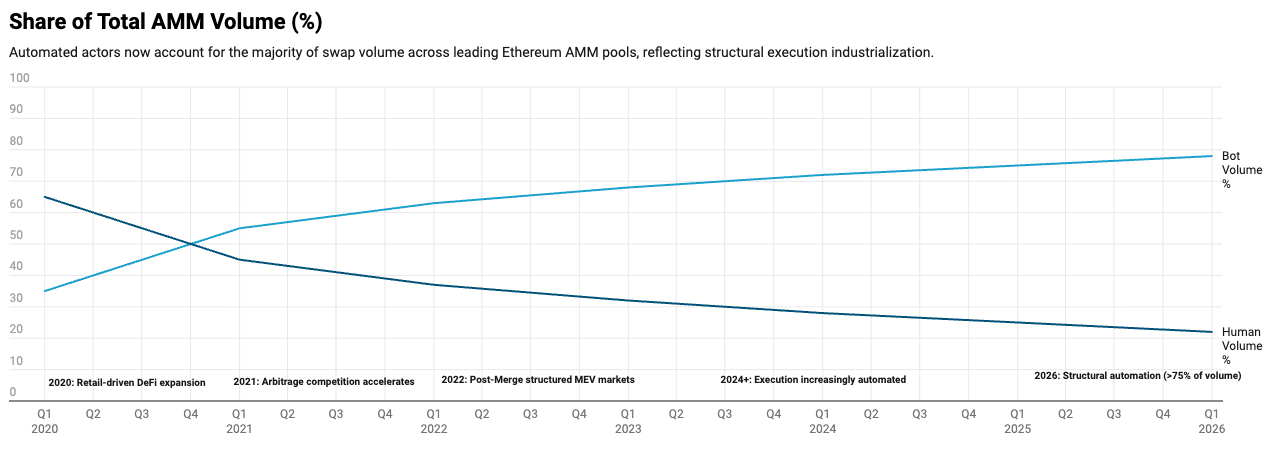
This is not a security flaw. It is a market design outcome.
Transparency exposes transaction intent before settlement.
Intent becomes tradable information.
In traditional finance, such pre-trade information leakage would be heavily regulated. In crypto, it is algorithmically monetized.
3. Order Flow Migration: Private Routing as Standard Practice
More than 50% of Ethereum order flow is now routed through private relays or protection mechanisms such as Flashbots Protect and other Dark RPC solutions.
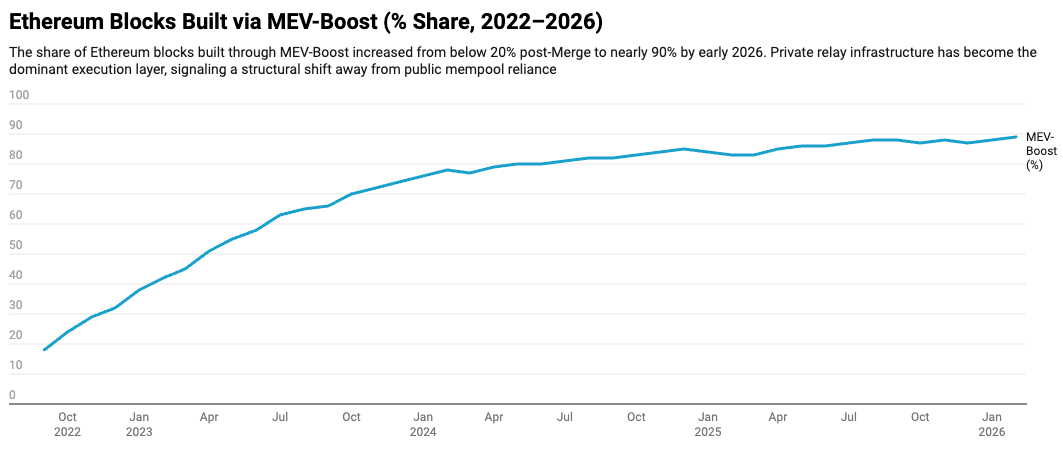
The motivation is not anonymity.
It is execution quality.
Private routing reduces:
Front-running probability
Sandwich exposure
Strategy leakage
In certain cases, routing through private infrastructure results in lower effective execution cost than public mempool submission.
This marks a structural shift:
The market is organically demanding confidentiality before regulation mandates it.
4. Case Study: Zcash and Shielded Adoption
Zcash offers a useful behavioral indicator of privacy demand.
As of February 2026:
Approximately 5 million ZEC (~30% of circulating supply) reside in shielded pools. This suggests privacy features are not merely ideological, they are behaviorally adopted when available.
This represents a substantial increase from roughly 11% in 2023.
This growth suggests that privacy features are being utilized rather than merely priced speculatively.
The broader takeaway is not about Zcash alone.
It is about demonstrated user preference when confidential settlement is available.
5. The Institutional Constraint: Transparency vs Strategy
For institutions, value does not reside solely in token balances. It resides in:
Execution logic
Liquidity routing models
Risk algorithms
Arbitrage frameworks
Market-making parameters
In transparent execution environments, these become attack surfaces.
A quant strategy revealed through transaction pattern visibility can be reverse-engineered.
A liquidation threshold observed publicly can be targeted.
A treasury rebalance can be anticipated.
This creates a paradox:
The more sophisticated the participant, the more damaging full transparency becomes.
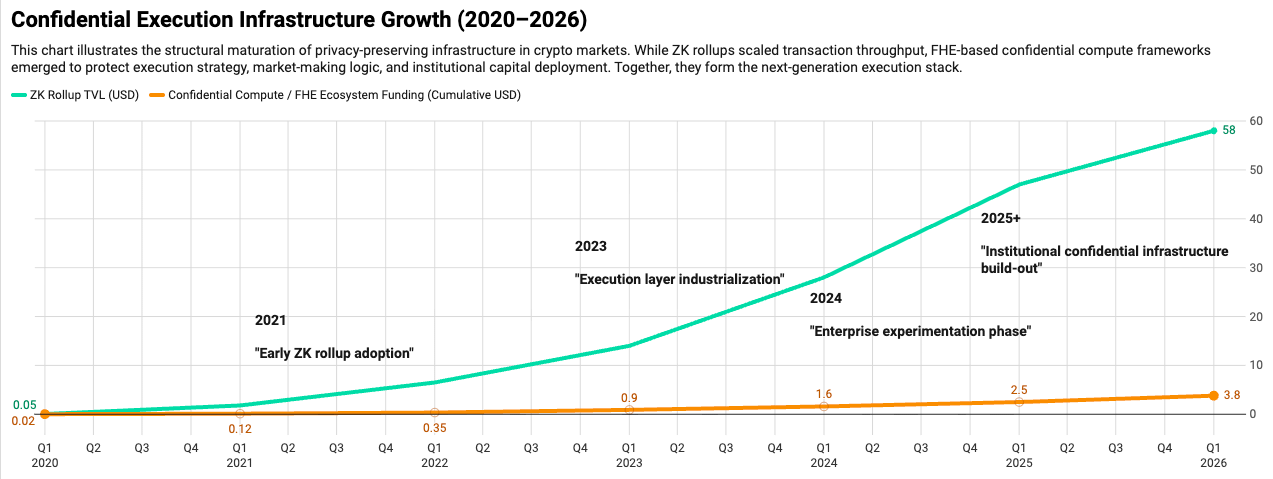
6. Zero-Knowledge and Fully Homomorphic Encryption: A Layered Thesis
Zero-Knowledge: Verifiable State without Data Exposure
Zero-Knowledge systems enable proof of correctness without revealing underlying inputs.
ZK-rollups now secure tens of billions in assets and allow scalable verification with reduced data disclosure. Compliance-compatible constructs such as view keys and programmable disclosure further align ZK systems with regulatory requirements.
ZK primarily protects the verification layer.
It ensures:
Valid state transitions
Public auditability
Mathematical correctness
However, ZK alone does not fully prevent execution leakage if inputs are observable before proof generation.
Fully Homomorphic Encryption: Confidential Computation
Fully Homomorphic Encryption allows computation directly on encrypted inputs without decryption during execution.
If ZK answers:
“How do we prove correctness without revealing data?”
FHE answers:
“How do we compute without revealing data at all?”
For institutional applications, this distinction is critical.
FHE enables:
Encrypted order matching
Confidential auctions
Private credit scoring
Strategy-protected smart contract execution
Secure AI inference on-chain
The computational overhead remains non-trivial. Latency and hardware requirements limit universal adoption. However, hybrid architectures (FHE execution + ZK verification) are emerging as viable models for high-value workflows.
Integrated Architecture: Verifiable Confidentiality
A forward-looking confidential stack includes:
Encrypted transaction inputs (FHE layer)
Encrypted computation within smart contracts
Zero-Knowledge proofs verifying correctness
Selective disclosure mechanisms for compliance
Conditional regulatory auditability
This model preserves decentralization while minimizing economic leakage.
It does not eliminate transparency.
It refines it.
7. Regulatory Convergence: From Anonymity to Selective Privacy
Post-Tornado Cash enforcement and the global rollout of frameworks such as MiCA have shifted design philosophy.
The dominant model is no longer “total anonymity.”
It is Selective Privacy, where:
Execution data is shielded
Proof of correctness remains public
Regulatory access can be conditionally enabled
This framework is far more compatible with institutional capital.
TradFi protects information via legal contracts.
Crypto increasingly protects information via cryptography.
8. Structural Implications for Market Design
As capital density increases:
Public mempools become economically inefficient
Transparent execution increases hidden transaction cost
MEV becomes a structural tax
Privacy infrastructure reduces:
Slippage volatility
Strategy replication risk
Capital inefficiency
Over time, execution confidentiality may become as fundamental as signature verification.
9. Strategic Outlook
Crypto is transitioning from ideological transparency to engineered confidentiality.
The evolution is predictable:
Phase 1: Radical transparency to bootstrap trust
Phase 2: Capital concentration and extraction
Phase 3: Cryptographic confidentiality with verifiability
Privacy is not a reactionary feature.
It is deferred infrastructure.
As ZK matures and FHE becomes computationally viable at scale, blockchains will no longer be defined by what they reveal, but by how efficiently they protect economic intent while preserving public correctness.
For institutional adoption, this is not optional.
It is structural.
This material is for informational purposes only and does not constitute investment advice.
Sources:
DefiLlama, Etherscan, Flashbots, mevboost.pics, Dune Analytics, public funding disclosures (2020–2026).

